Hacking domain controller with zerologon vulnerability CVE-2020-1472

In this how to we are showing the exploitation of CVE-2020-1472 also name the zerologon vulnerability. Zerologon is a vulnerability in the cryptography of Microsoft’s Netlogon process that allows an attack against Microsoft Active Directory domain controllers. Zerologon makes it possible for a hacker to impersonate any computer, including the root domain controller. Requirements: Install […]
Securing unused domains

A lot of companies have reserved more than one domain name for their organization. Multiple of those domain name are not been used for email purpose but are a target for hackers to use them for phishing attacks. It’s highly recommended to have at least some basic DNS records to protect the domain name for […]
Effectieve scope voor penetratie testen

Vaak wordt door organisaties het bepalen van de scope voor een penetratie test onderschat. Het niet juist scopen van een opdracht kan resulteren in bijvoorbeeld een niet volledige test of dat er onvoldoende diepgang is geweest. Het is dus van belang om een juiste scope vast te stellen tijdens het intake gesprek en dat de […]
Fail2Ban log monitoring and blocking application
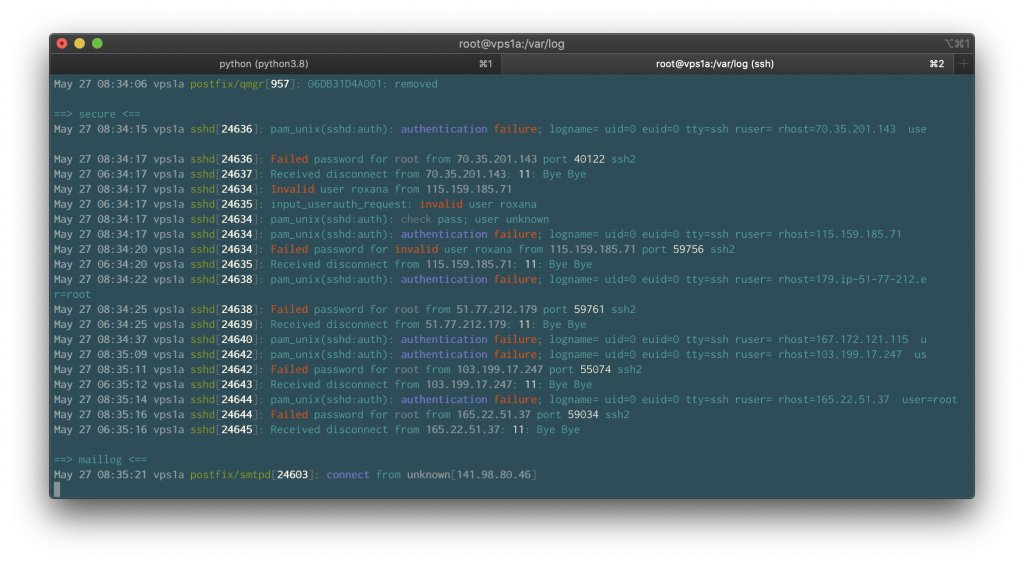
Lot’s of systems on the internet are been hacked trough the use of easy guessable passwords or default credentials. In many cases the source ip address is been hacked the same way. Attackers are pivoting through compromised systems. Fail2ban is an application that monitored your log files and based on pre defined thresholds fail2ban will […]
Securing WordPress with .htaccess
Why Website Security is Important? A hacked WordPress site can cause serious damage to your business revenue and reputation. Hackers can steal user information, passwords, install malicious software, and can even distribute malware to your users. Worst, you may find yourself paying ransomware to hackers just to regain access to your website. How to Disable […]
GoPhish
What is Gophish? Gophish is a phishing framework that makes the simulation of real-world phishing attacks dead-simple. The idea behind gophish is simple – make industry-grade phishing training available to everyone. “Available” in this case means two things – Affordable – Gophish is open-source software that is completely free for anyone to use. Accessible – […]
